总部采用安全策略组与分支建立多条IPSec隧道
1.项目情况
1.总部和分部路由器都有固定的公网地址
2.总部和分部使用不同的IPSec安全策略
2.拓扑图
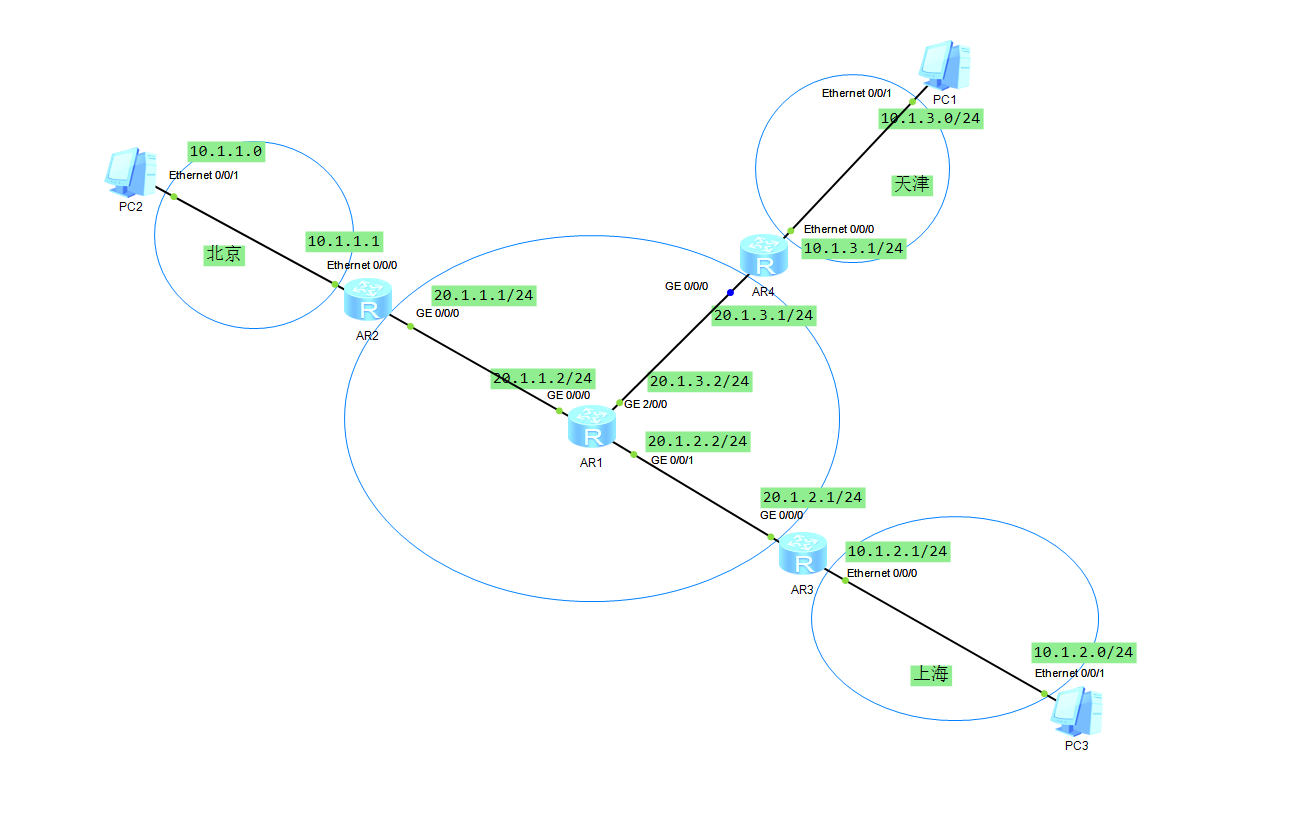
3.基础环境搭建
R1
<Huawei>sys
[Huawei]sys R1
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]ip add 20.1.1.2 24
[R1-GigabitEthernet0/0/0]int g0/0/1
[R1-GigabitEthernet0/0/1]ip add 20.1.2.2 24
[R1-GigabitEthernet0/0/1]int g2/0/0
[R1-GigabitEthernet2/0/0]ip add 20.1.3.2 24
R2
<Huawei>sys
[Huawei]sys R2
[R2]int g0/0/0
[R2-GigabitEthernet0/0/0]ip address 20.1.1.1 24
[R2-GigabitEthernet0/0/0]int vlanif 1
[R2-Vlanif1]ip address 10.1.1.1 24
[R2]ip route-static 20.1.3.0 24 20.1.1.2
[R2]ip route-static 20.1.2.0 24 20.1.1.2
R3
<Huawei>sys
[Huawei]sys R3
[R3]int g0/0/0
[R3-GigabitEthernet0/0/0]ip add 20.1.2.1 24
[R3-GigabitEthernet0/0/0]int vlanif1
[R3-Vlanif1]ip add 10.1.2.1 24
[R3]ip route-static 20.1.3.0 24 20.1.2.2
[R3]ip route-static 20.1.1.0 24 20.1.2.2
R4
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]sys R4
[R4]int g0/0/0
[R4-GigabitEthernet0/0/0]ip add 20.1.3.1 24
[R4-GigabitEthernet0/0/0]int vlanif1
[R4-Vlanif1]ip add 10.1.3.1 24
[R4]ip route-static 20.1.1.0 24 20.1.3.2
[R4]ip route-static 20.1.2.0 24 20.1.3.2
连通性测试
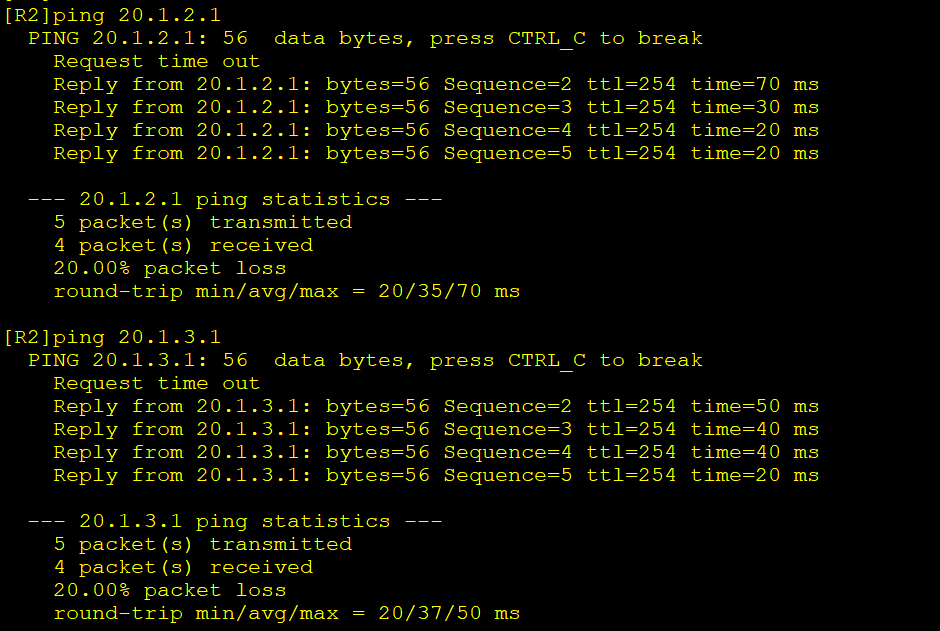
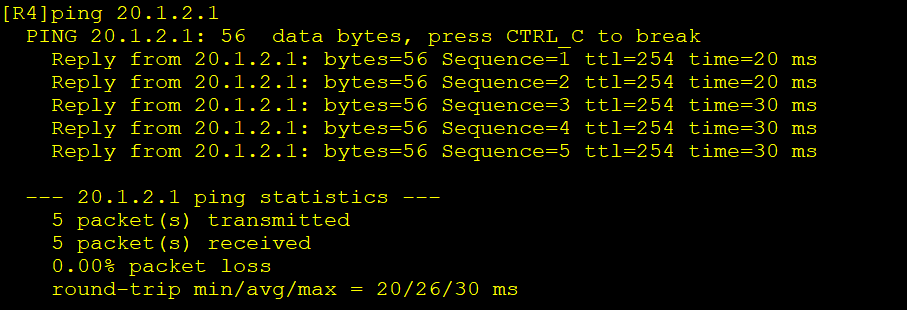
4.在总部路由器上设置-R2
[R2]acl 3100
[R2-acl-adv-3100]rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.3.0 0.0.0.255
[R2-acl-adv-3100]quit
[R2]acl 3200
[R2-acl-adv-3200]rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
[R2-acl-adv-3200]quit
[R2]ipsec proposal prol
[R2-ipsec-proposal-prol]quit
[R2]ike peer rut1 v2
[R2-ike-peer-rut1]pre-shared-key simple 91xueit
[R2-ike-peer-rut1]remote-address 20.1.3.1
[R2-ike-peer-rut1]quit
[R2]ike peer rut2 v2
[R2-ike-peer-rut2]pre-shared-key simple 51cto
[R2-ike-peer-rut2]remote-address 20.1.2.1
[R2-ike-peer-rut2]quit
[R2]ipsec policy policy1 10 isakmp
[R2-ipsec-policy-isakmp-policy1-10]ike-peer rut1
[R2-ipsec-policy-isakmp-policy1-10]proposal prol
[R2-ipsec-policy-isakmp-policy1-10]security acl 3100
[R2-ipsec-policy-isakmp-policy1-10]quit
[R2]ipsec policy policy1 20 isakmp
[R2-ipsec-policy-isakmp-policy1-20]ike-peer rut2
[R2-ipsec-policy-isakmp-policy1-20]proposal prol
[R2-ipsec-policy-isakmp-policy1-20]security acl 3200
[R2-ipsec-policy-isakmp-policy1-20]quit
[R2]int g0/0/0
[R2-GigabitEthernet0/0/0]ipsec policy policy1
[R2-GigabitEthernet0/0/0]quit
[R2]ip route-static 10.1.2.0 24 20.1.1.2
[R2]ip route-static 10.1.3.0 24 20.1.1.2
R4
<R4>sys
[R4]acl 3100
[R4-acl-adv-3100]rule permit ip source 10.1.3.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[R4-acl-adv-3100]quit
[R4]ipsec proposal prop
[R4-ipsec-proposal-prop]quit
[R4]ike peer rut1 v2
[R4-ike-peer-rut1]pre-shared-key simple 91xueit
[R4-ike-peer-rut1]remote-address 20.1.1.1
[R4-ike-peer-rut1]quit
[R4]ipsec policy policy1 10 isakmp
[R4-ipsec-policy-isakmp-policy1-10]ike-peer rut1
[R4-ipsec-policy-isakmp-policy1-10]proposal prop
[R4-ipsec-policy-isakmp-policy1-10]security acl 3100
[R4-ipsec-policy-isakmp-policy1-10]quit
[R4]int g0/0/0
[R4-GigabitEthernet0/0/0]ipsec policy policy1
[R4-GigabitEthernet0/0/0]quit
[R4]ip route-static 10.1.1.0 24 20.1.3.2
R3
<R3>sys
[R3]acl 3000
[R3-acl-adv-3000]rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[R3-acl-adv-3000]ipsec propo
[R3-acl-adv-3000]quit
[R3]ipsec proposal prop
[R3-ipsec-proposal-prop]quit
[R3]ike peer rut1 v2
[R3-ike-peer-rut1]pre-shared-key simple 51cto
[R3-ike-peer-rut1]remote-address 20.1.1.1
[R3-ike-peer-rut1]quit
[R3]ipsec policy policy1 10 isakmp
[R3-ipsec-policy-isakmp-policy1-10]ike-peer rut1
[R3-ipsec-policy-isakmp-policy1-10]security acl 3000
[R3-ipsec-policy-isakmp-policy1-10]proposal prop
[R3-ipsec-policy-isakmp-policy1-10]quit
[R3]interface GigabitEthernet 0/0/0
[R3-GigabitEthernet0/0/0]ipsec policy policy1
[R3-GigabitEthernet0/0/0]quit
[R3]ip route-static 10.1.1.0 24 20.1.2.2
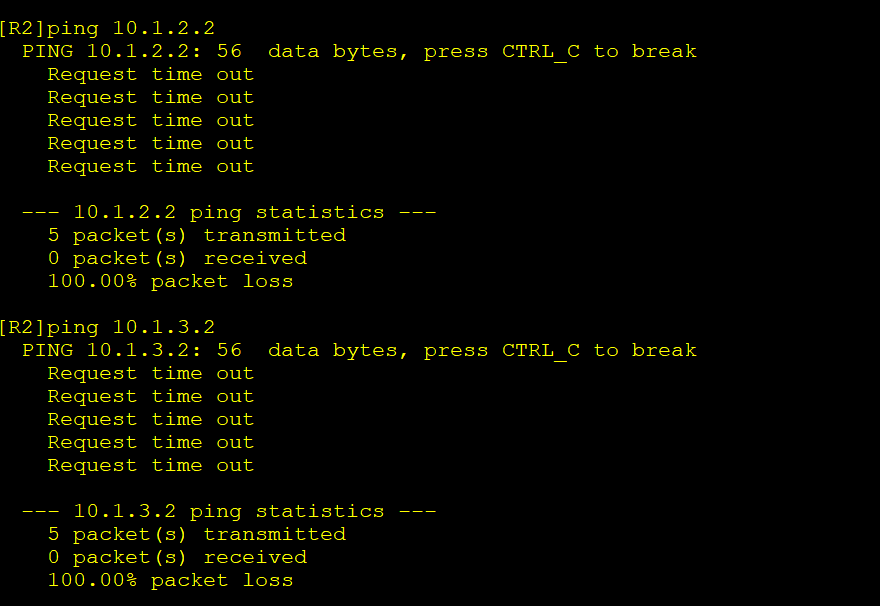
5.测试连通性
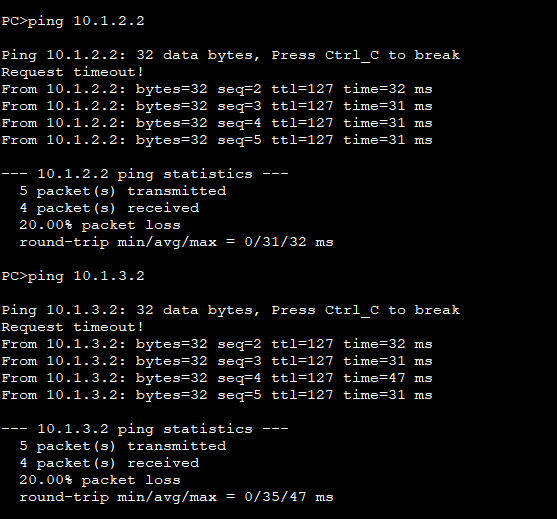
6.配置让两个分公司通过总公司IPSec-VPN通信
由于两个对等识别密码都不一样,所以,R3和R4是不能通过添加访问控制列表和路由而实现通讯