Contents
基于ACL手工创立IPSEC隧道
1.拓扑图
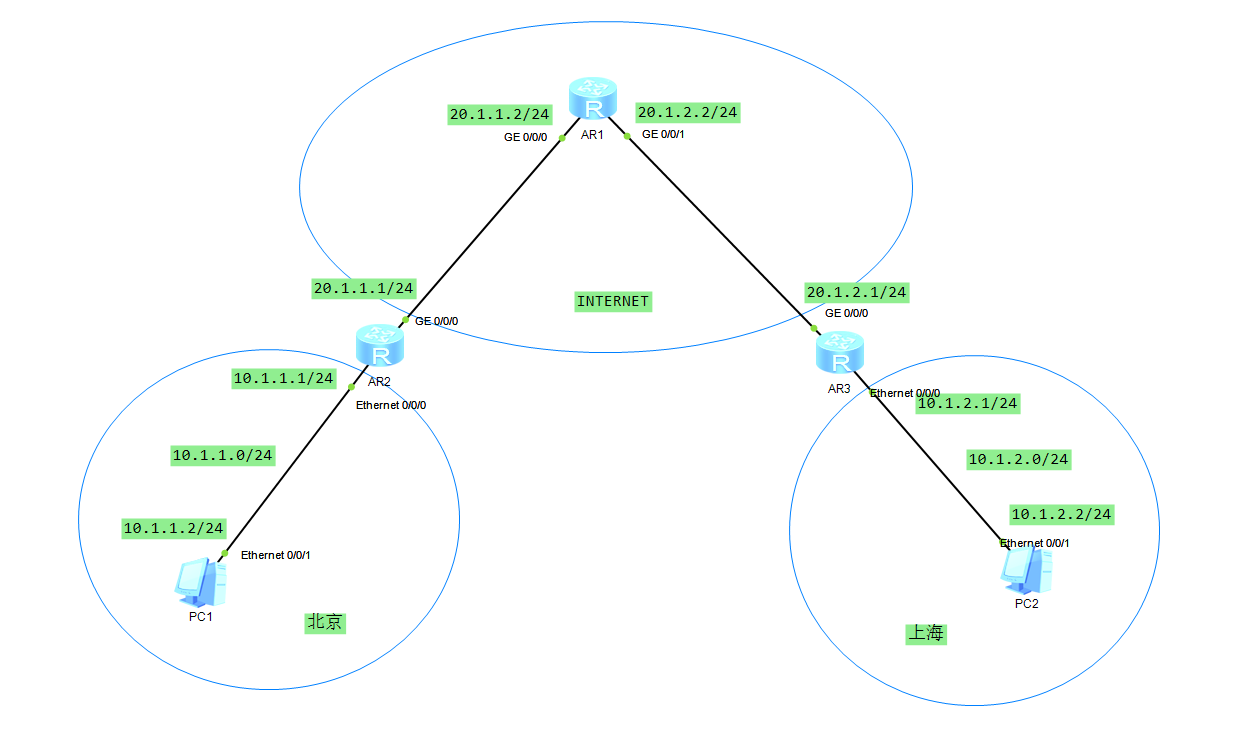
2.配置R1
<Huawei>sys
[Huawei]sys R1
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]ip add 20.1.1.2 24
[R1-GigabitEthernet0/0/0]int g0/0/1
[R1-GigabitEthernet0/0/1]ip add 20.1.2.2 24
3.配置R2
<Huawei>sys
[Huawei]sys R2
[R2]int g0/0/1
[R2-GigabitEthernet0/0/1]ip add 10.1.1.1 24
[R2]interface vlanif1
[R2-Vlanif1]ip address 10.1.1.1 24
[R2]ip route-static 20.1.2.0 24 20.1.1.2
4.配置R3
<Huawei>sys
[Huawei]sys R3
[R3]int g0/0/0
[R3-GigabitEthernet0/0/0]ip add 20.1.2.1 24
[R3]int vlanif1
[R3-Vlanif1]ip address 10.1.2.1 24
[R3]ip route-static 20.1.1.0 24 20.1.2.2
5.连通性测试
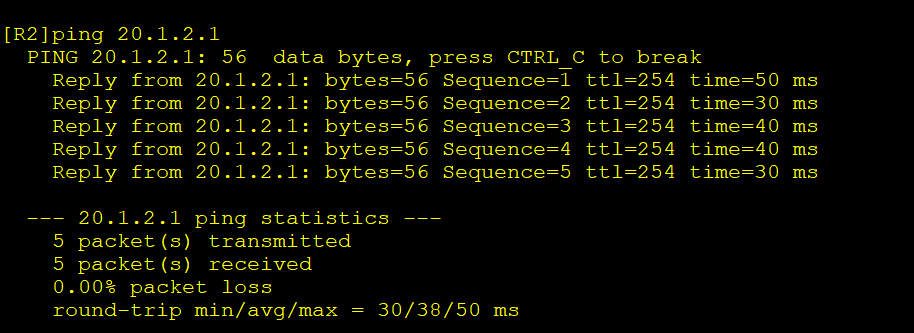
6.创建IPSEC隧道-ESP加密
6.1.定义ACL-R2
[R2]acl 3100
[R2-acl-adv-3100]rule per
[R2-acl-adv-3100]rule permit ip sour
[R2-acl-adv-3100]rule permit ip source 10.1.1.0 0.0.0.255 de
[R2-acl-adv-3100]rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0
.0.0.255
[R2-acl-adv-3100]rule deny ip
[R2-acl-adv-3100]quit
6.2.配置安全提议-R2
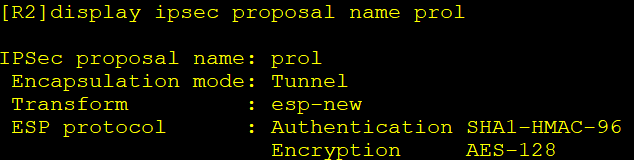
[R2]ipsec proposal prol
[R2-ipsec-proposal-prol]esp authentication-algorithm sha1
[R2-ipsec-proposal-prol]esp encryption-algorithm aes-128
[R2-ipsec-proposal-prol]quit
[R2]display ipsec proposal name prol
6.3.创建IPSEC隧道-R2
[R2]ipsec policy client 10 manual
[R2-ipsec-policy-manual-client-10]security acl 3100
[R2-ipsec-policy-manual-client-10]proposal prol
[R2-ipsec-policy-manual-client-10]tunnel remote 20.1.2.1
[R2-ipsec-policy-manual-client-10]tunnel local 20.1.1.1
[R2-ipsec-policy-manual-client-10]sa spi outbound esp 12345
[R2-ipsec-policy-manual-client-10]sa spi inbound esp 54321
[R2-ipsec-policy-manual-client-10]sa string-key outbound esp simple 91xueit
[R2-ipsec-policy-manual-client-10]sa string-key inbound esp simple 51cto
[R2-ipsec-policy-manual-client-10]sa encryption-hex inbound esp simple 12345678
90abcdef1234567890abcdef #与sa string-key只能二选一
[R2-ipsec-policy-manual-client-10]sa encryption-hex outbound esp simple abcdef1
234567890abcdef1234567890 #与sa string-key只能二选一
[R2-ipsec-policy-manual-client-10]quit
6.4.将策略绑定到接口-R2
[R2]interface GigabitEthernet 0/0/0
[R2-GigabitEthernet0/0/0]ipsec policy client
6.5.添加到远端的路由-R2
[R2]ip route-static 10.1.2.0 24 20.1.1.2
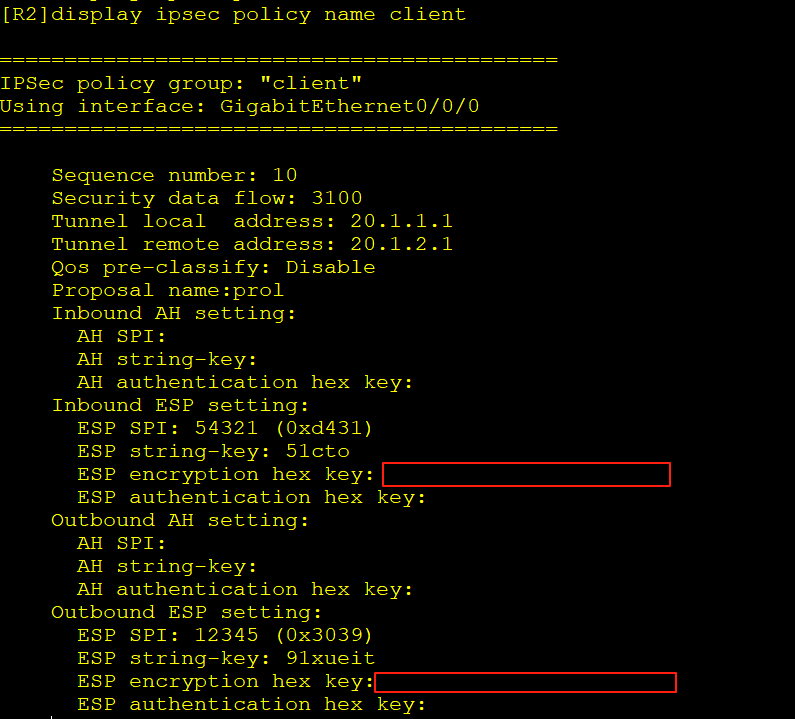
6.6.查看创建的IPSec策略-R2
[R2]display ipsec policy name client
6.7.定义ACL-R3
<R3>sys
[R3]acl 3100
[R3-acl-adv-3100]rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[R3-acl-adv-3100]rule deny ip
[R3-acl-adv-3100]quit
6.8.配置安全提议-R3
[R3]ipsec proposal prol
[R3-ipsec-proposal-prol]esp authentication-algorithm sha1
[R3-ipsec-proposal-prol]esp encryption-algorithm aes-128
[R3-ipsec-proposal-prol]quit
6.9.创建IPSEC隧道-R3
[R3]ipsec policy server 10 manual
[R3-ipsec-policy-manual-server-10]security acl 3100
[R3-ipsec-policy-manual-server-10]proposal prol
[R3-ipsec-policy-manual-server-10]tunnel remote 20.1.1.1
[R3-ipsec-policy-manual-server-10]tunnel local 20.1.2.1
[R3-ipsec-policy-manual-server-10]sa spi inbound esp 12345
[R3-ipsec-policy-manual-server-10]sa spi outbound esp 54321
[R3-ipsec-policy-manual-server-10]sa string-key outbound esp simple 51cto
[R3-ipsec-policy-manual-server-10]sa string-key inbound esp simple 91xueit
[R3-ipsec-policy-manual-server-10]sa encryption-hex outbound esp simple 12345678
90abcdef1234567890abcdef #与sa string-key只能二选一
[R3-ipsec-policy-manual-server-10]sa encryption-hex inbound esp simple abcdef123
4567890abcdef1234567890 #与sa string-key只能二选一
[R3-ipsec-policy-manual-server-10]quit
[R3]interface GigabitEthernet 0/0/0
[R3-GigabitEthernet0/0/0]ipsec policy server
ip route-static 10.1.1.0 24 20.1.2.2
6.10.将策略绑定到接口-R3
[R3]interface GigabitEthernet 0/0/0
[R3-GigabitEthernet0/0/0]ipsec policy server
6.11.添加到远端的路由-R3
[R3]ip route-static 10.1.1.0 24 20.1.2.2
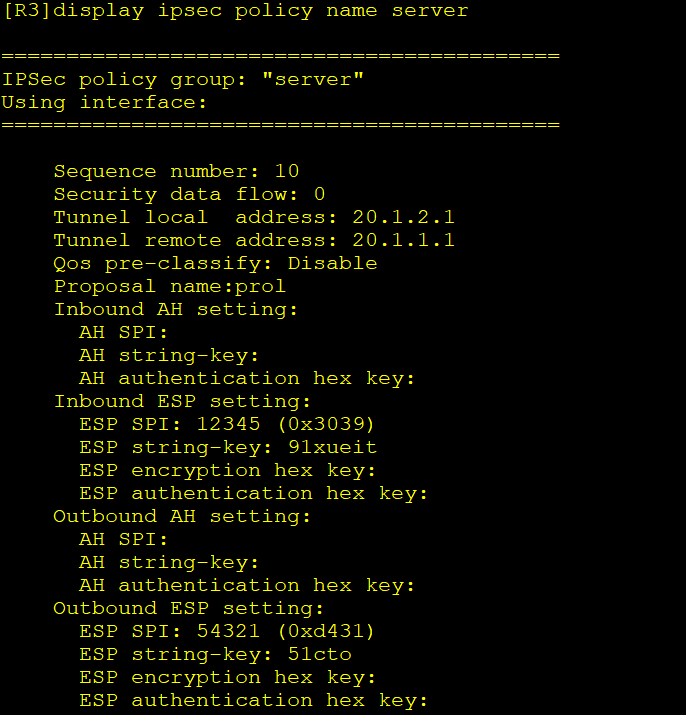
6.12.查看创建的IPSec策略-R3
[R2]display ipsec policy name server
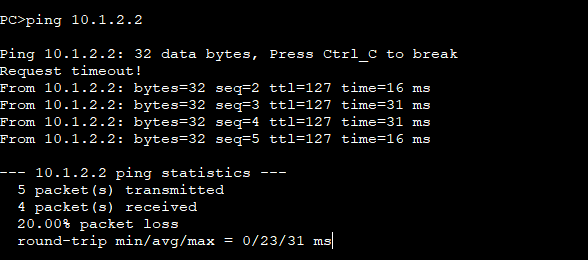
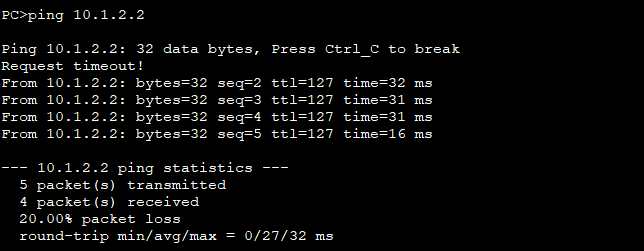
7.测试与抓包
PC1 PING 通 PC2
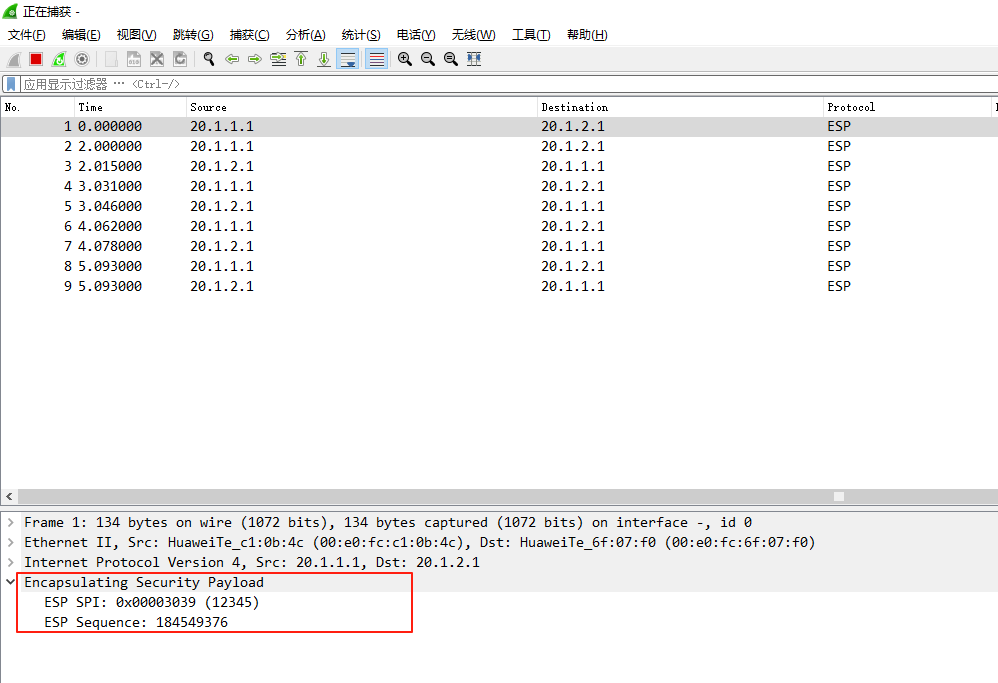
抓包
只看到ESP这一层
8.注意点
8.1.sa string-key 和 sa encryption-hex不能同时使用
在华为设备的IPsec配置中,ESP的字符串密钥 (sa string-key) 和加密十六进制密钥 (sa encryption-hex) 不能同时配置用于同一方向(入站或出站)的相同协议(如ESP)。
核心原因:*
- 二选一原则:
sa string-key和sa encryption-hex都是为了配置相同的密钥参数(在这里是ESP加密密钥)。- 设备需要确定使用哪一种格式的密钥来生成实际的加密密钥。同时配置两者会产生歧义,设备无法决定使用哪个值。
- 本质上,它们是配置同一个东西(ESP加密密钥)的两种不同输入方式。
正确的做法:
- 明确选择一种密钥输入方式:
sa string-key ...: 使用明文字符串(如91xueit,51cto)。设备内部会将该字符串转换为实际用于加密算法的二进制密钥。优势是配置简单易记,缺点是密钥复杂度相对较低(受限于可输入字符),且明文显示在配置中(安全风险)。sa encryption-hex ...: 直接输入所需长度的加密密钥的十六进制表示(如1234567890abcdef1234567890abcdef对于AES-128是32个字符,即128位)。优势是密钥复杂度和随机性可以非常高(直接定义二进制密钥),且不会因字符串转换引入额外处理。缺点是配置复杂,需要手动计算或生成正确长度的十六进制串,不易记忆。
- 为每个方向(入站/出站)的ESP只配置一次密钥: 要么用
string-key,要么用encryption-hex,不能两者都用。
结论:
ESP的字符串密钥 (sa string-key) 和加密十六进制密钥 (sa encryption-hex) 只能二选一配置,不能同时用于同一方向上的ESP。 同时配置属于错误配置,虽然在某些设备版本上可能因为内部处理机制(覆盖/忽略其中一个)而侥幸让隧道工作(如你的例子),但这并不是标准、可靠或推荐的做法。为了保证配置的正确性和可维护性,应该严格按照二选一的原则进行配置,并确保两端使用相同的密钥格式和匹配的密钥值。在你的配置中,删除所有 sa string-key ... esp ... 命令,只保留 sa encryption-hex ... esp ... 命令是最规范的做法。
9.创建新的安全提议(AH+ESP)
9.1.创建新的安全提议(组合AH+ESP):
# 在R2上
[R2] ipsec proposal ah_esp_proposal
[R2-ipsec-proposal-ah_esp_proposal] transform ah-esp # 关键:指定组合模式
[R2-ipsec-proposal-ah_esp_proposal] ah authentication-algorithm sha2-256
[R2-ipsec-proposal-ah_esp_proposal] esp authentication-algorithm sha1
[R2-ipsec-proposal-ah_esp_proposal] esp encryption-algorithm aes-128
[R2-ipsec-proposal-ah_esp_proposal] quit
# 在R3上
[R3] ipsec proposal ah_esp_proposal
[R3-ipsec-proposal-ah_esp_proposal] transform ah-esp # 关键:指定组合模式
[R3-ipsec-proposal-ah_esp_proposal] ah authentication-algorithm sha2-256
[R3-ipsec-proposal-ah_esp_proposal] esp authentication-algorithm sha1
[R3-ipsec-proposal-ah_esp_proposal] esp encryption-algorithm aes-128
[R3-ipsec-proposal-ah_esp_proposal] quit
9.2.更新IPsec策略引用新提议:
# R2更新策略
[R2] ipsec policy client 10 manual
[R2-ipsec-policy-manual-client-10] undo proposal # 替换原有提议
[R2-ipsec-policy-manual-client-10] proposal ah_esp_proposal
[R2-ipsec-policy-manual-client-10] quit
# R3更新策略
[R3] ipsec policy server 10 manual
[R3-ipsec-policy-manual-server-10] undo proposal # 替换原有提议
[R3-ipsec-policy-manual-server-10] proposal ah_esp_proposal
[R3-ipsec-policy-manual-server-10] quit
9.3.添加AH的SPI和密钥配置:
# R2添加AH参数
[R2] ipsec policy client 10 manual
[R2-ipsec-policy-manual-client-10] sa spi outbound ah 67890
[R2-ipsec-policy-manual-client-10] sa spi inbound ah 98765
[R2-ipsec-policy-manual-client-10]sa authentication-hex outbound ah simple 11223
344556677889900aabbccddeeff11223344556677889900aabbccddeeff
[R2-ipsec-policy-manual-client-10]sa authentication-hex inbound ah simple aabbcc
ddeeff00112233445566778899aabbccddeeff00112233445566778899
[R2-ipsec-policy-manual-client-10] quit
# R3添加AH参数(确保对称配置)
[R3] ipsec policy server 10 manual
[R3-ipsec-policy-manual-server-10] sa spi outbound ah 98765 # 匹配R2的inbound
[R3-ipsec-policy-manual-server-10] sa spi inbound ah 67890 # 匹配R2的outbound
[R3-ipsec-policy-manual-server-10]sa authentication-hex outbound ah simple aabbc
cddeeff00112233445566778899aabbccddeeff00112233445566778899
[R3-ipsec-policy-manual-server-10]sa authentication-hex inbound ah simple 112233
44556677889900aabbccddeeff11223344556677889900aabbccddeeff
[R3-ipsec-policy-manual-server-10] quit
9.4.重新应用策略:
# R2重新应用策略
[R2] interface GigabitEthernet 0/0/0
[R2-GigabitEthernet0/0/0] ipsec policy client
# R3重新应用策略
[R3] interface GigabitEthernet 0/0/0
[R3-GigabitEthernet0/0/0] ipsec policy server
9.5.验证配置:
# 检查安全提议
[R2] display ipsec proposal name ah_esp_proposal
# 检查IPsec策略
[R2] display ipsec policy name client
测试:
PC1 PING通 PC2
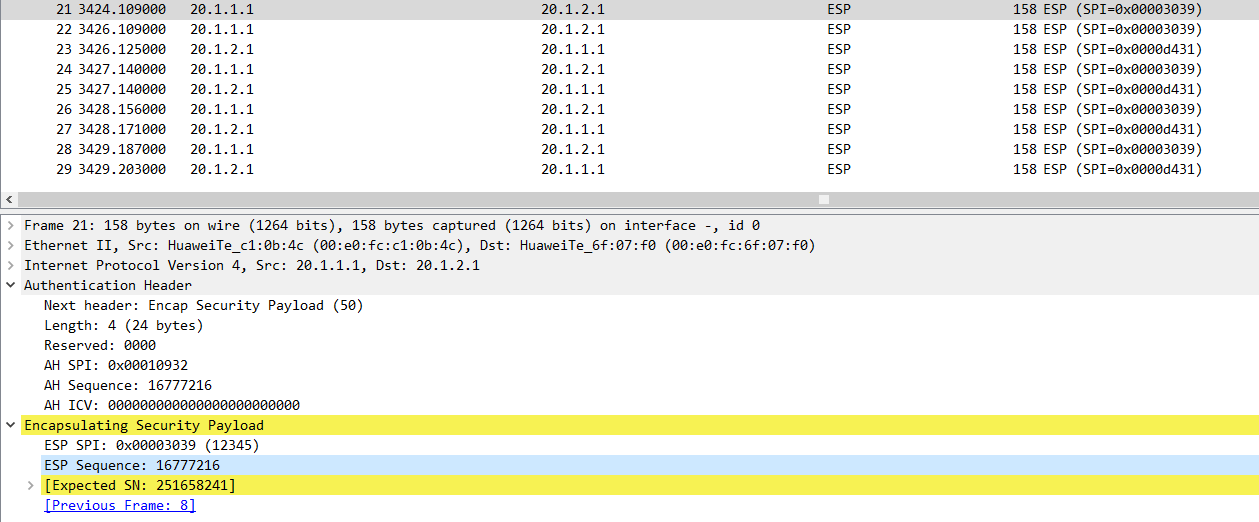
抓包
配置完成后,流量将受到AH和ESP的双重保护。在抓包分析中,您将看到AH头(协议号51)和ESP头(协议号50)同时出现在IP数据包中。
10.关键注意事项:
- 转换类型(Transform Type):
- 必须使用
transform ah-esp明确指定组合模式 - 可选值:
ah、esp或ah-esp
- 必须使用
- 处理顺序:
- 出站流量:先应用AH认证,然后ESP加密
- 入站流量:先ESP解密,然后AH验证
- AH密钥要求:
- SHA2-256需要256位密钥(64个十六进制字符)
- 例如:
aabbccddeeff00112233445566778899(32字节)
- SPI冲突避免:
- AH和ESP的SPI必须不同
- 示例中AH使用6xxxx/9xxxx,ESP使用1xxxx/5xxxx